when i was a kid , i used to think that digital signature is just signature in Digital form(picture of signature). but i was wrong at all.
it's use is just the same like Normal signature (i.e to validate something) but form is different (i.e. digital)
so the definition of digital signature can be "A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents"
Digital signature has following prerequisites.
it's use is just the same like Normal signature (i.e to validate something) but form is different (i.e. digital)
so the definition of digital signature can be "A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents"
Digital signature has following prerequisites.
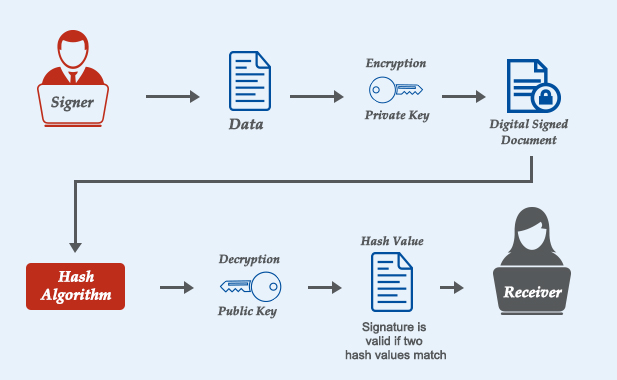
Received Message
Secure Hash Algorithm
Message Digest
Validation Algorithm
Digital Signature

Digital signatures can provide the added assurances of evidence of origin, identity and status of an electronic document, transaction or message and can acknowledge informed consent by the signer.

















